what security measure can be used to generate and store cryptographic keys
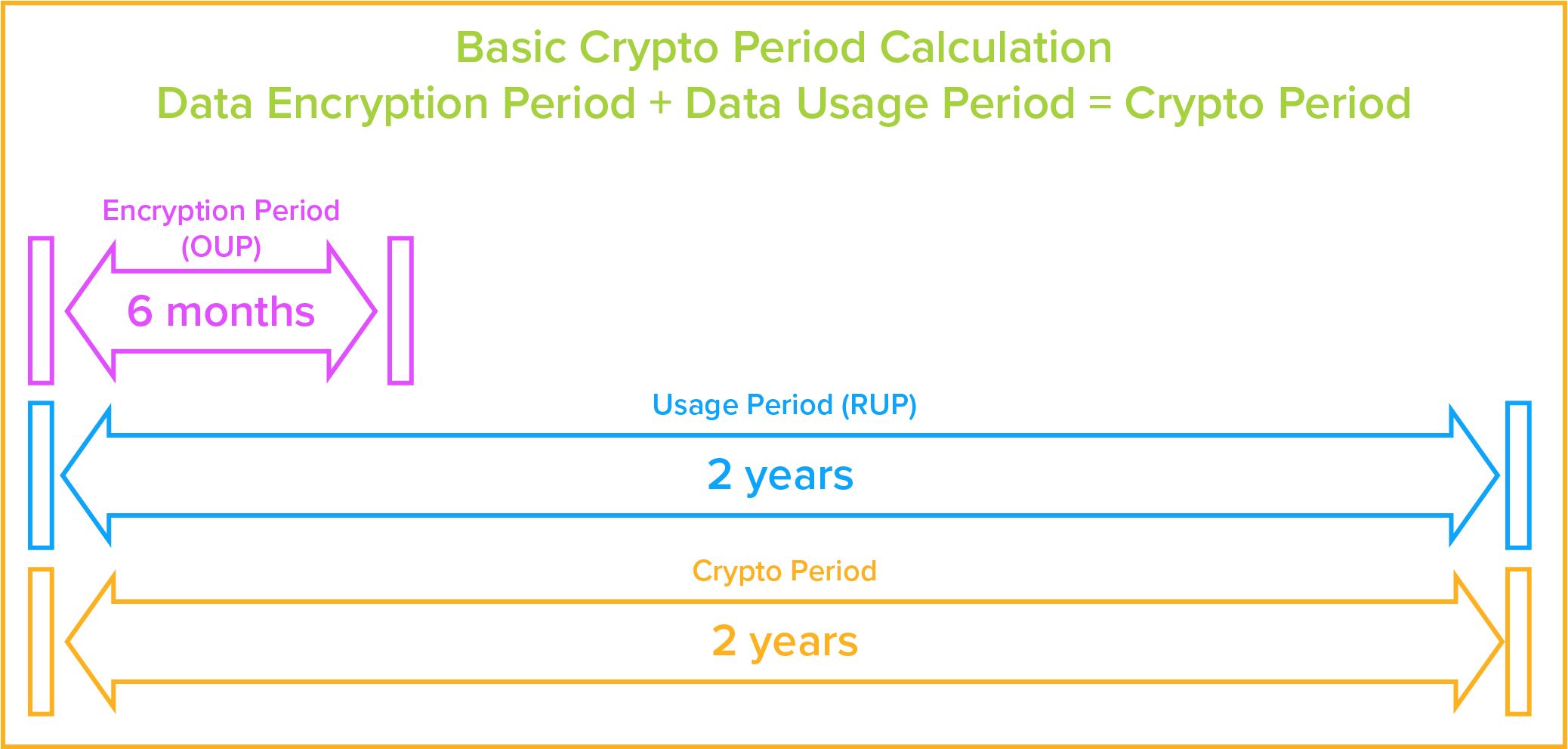
Encryption key direction is administering the total lifecycle of cryptographic keys. This includes: generating, using, storing, archiving, and deleting of keys. Protection of the encryption keys includes limiting access to the keys physically, logically, and through user/role access. ^Dorsum to Top Let'due south get started with a brief overview of the types of encryption keys. ^Back to Elevation In symmetric key cryptography, the same encryption key is used to both encrypt and decrypt the data. This means of encryption is used primarily to protect data at rest. An example would be to encrypt sensitive information into ciphertext while it is stored in a database and decrypt it to plaintext when it is accessed past an authorized user, and vice versa. Asymmetric keys, on the other hand, are a pair of keys for the encryption and decryption of the data. Both keys are related to each other and created at the same time. They are referred to every bit a public and a private key: ^Back to Top First, permit's found a few definitions: Now that we have the definitions in place, below is a pace by footstep case of how an authorized user accesses encrypted data: ^Back to Meridian The encryption fundamental life-bike, defined by NIST as having a pre-operational, operational, mail-operational, and deletion stages, requires that, amidst other things, a operational crypto flow be defined for each key. A crypto period is the "time span during which a specific primal is authorized for use" and in Section v.3 of NIST's Guide, the crypto period is adamant (for example, with a symmetric key) by combining the estimated time during which encryption will be practical to data (the Originator Usage Flow (OUP)) and the time when it will be decrypted for utilise (the Recipient Usage Flow (RUP)). And so, equally an instance: But, since an organization may reasonably desire to encrypt and decrypt the same data for years on finish, other factors may come into play to when factoring the crypto flow: Y'all may desire to limit the: This can be boiled down to a few key questions: The general rule: every bit the sensitivity of information being secured increases, the lifetime of an encryption key decreases. Given this, your encryption key may have an active life shorter than an authorized user'southward admission to the data. This means that you lot volition need to archive de-activated keys and use them but for decryption. Once the data has been decrypted past the old key, it will be encrypted past the new key, and over time the one-time central will no longer be usedto encrypt/decrypt data and tin exist deleted. (run into graphic beneath) See beneath for a more thorough agreement of a keys total life-cycle. The encryption fundamental is created and stored on the key management server. The key manager creates the encryption key through the use of a cryptographically secure random fleck generator and stores the key, along with all information technology's attributes, into the key storage database. The attributes stored with the key include its name, activation engagement, size, case, the power for the key to be deleted, as well as its rollover, mirroring, primal access, and other attributes. The key can be activated upon its creation or set to be activated automatically or manually at a later time. The encryption key manager should track current and past instances (or versions) of the encryption key. Yous need to be able to choose whether or not the key tin can be deleted, mirrored to a failover unit, and past which users or groups it can be accessed. Your cardinal manager should allow the ambassador to alter many of the central's attributes at any time. An ambassador should be able to use the central manager to revoke a key and so that it is no longer used for encryption and decryption requests. A revoked key can, if needed, be reactivated past an administrator then that, In certain cases the fundamental can be used to decrypt data previously encrypted with information technology, like erstwhile backups. But even that can be restricted. NIST (Section eight.3.ane) requires that an archive should be kept for deactivated keys. The archive should "protect the archived textile from unauthorized [disclosure,] modification, deletion, and insertion." The encryption keys need "to be recoverable … after the end of its cryptoperiod" and "the system shall exist designed to allow reconstruction" of the keys should they need to be reactivated for utilize in decrypting the information that information technology once encrypted. If a key is no longer in use or if it has somehow been compromised, an administrator can choose to delete the key entirely from the key storage database of the encryption key director. The primal director will remove it and all its instances, or just sure instances, completely and brand the recovery of that key impossible (other than through a restore from a fill-in image). This should exist available as an choice if sensitive information is compromised in its encrypted state. If the cardinal is deleted, the compromised data will be completely secure and unrecoverable since it would be impossible to recreate the encryption fundamental for that information. ^Back to Top In "Recommendation for Key Management – Role ii" NIST defines Separation of Duties as: The practice of Separation of Duties reduces the potential for fraud or malfeasance by dividing related responsibilities for disquisitional tasks betwixt different individuals in an organisation. Information technology is common in the financial and accounting procedures of most organizations. For example, the person who prints the checks at a company would not exist the person who signs the checks. Similarly, the individual who signs checks would not reconcile the banking company statements. A visitor would ensure that business critical duties are categorized into four types of functions: authorization, custody, tape keeping, and reconciliation. In a perfect system, no ane person should handle more than ane blazon of function. Regarding information security practices, the implementation of Separation of Duties is critical in the area of encryption central management. To prevent unwanted access to protected data, information technology is important that the person who manages encryption keys non have the ability to access protected data, and vice versa. This is no more than difficult to reach in an information technology context than in a financial context, but is often overlooked or misunderstood in complex estimator systems. Again, NIST, in Recommendation for Key Management – Part two, defines Dual Control: While Separation of Duties involves distributing different parts of a process to unlike people, Dual Control requires that at to the lowest degree 2 or more individuals control a single process. In data security do it is common to find requirements for Dual Control of encryption key management functions. Because a cardinal management system may be storing encryption keys for multiple applications and business organisation entities, the protection of encryption keys is critically important. The concept of Dissever Knowledge applies to whatsoever admission or handling of unprotected cryptographic material like encryption keys or passphrases used to create encryption keys, and requires that no one person know the consummate value of an encryption key. If passphrases are used to create encryption keys, no 1 person should know the entire passphrase. Rather, 2 or more people should each know only a part of the pass phrase, and all of them would have to be present to create or recreate an encryption key. ^Dorsum to Top Many, when talking about securing a fundamental managing director, will naturally turn to securing the primal manager itself with a hardware security module (HSM). While that is a necessary topic (and we will discuss information technology), nosotros should offset talk about securing the physical environment in which your key manager is housed. In NIST's Special Publication 800-14, they offering this definition of physical security: An organization's concrete security programme need to include things like: Now comes securing the cryptographic module itself. The Federal Information Processing Standards (FIPS) has identified four levels of increasing security in FIPS 140-two that tin can be applied to the module, each corresponding to the commensurate threat level: Every data security product available makes claims equally to superior functionality or information protection. But when protecting sensitive information, organizations need to have balls that a product'southward stated security claim is valid. This is certainly true when it comes to an encryption cardinal director. To address this, NIST has devised a organisation to validate cryptographic modules and ensure that they comply with FIPS 140-ii standards. Here are the steps an encryption fundamental manager vendor must to take to testify total compliance: The side by side loonshit in which you tin can protect your encryption keys is past logically separating the dissimilar cryptographic components housing the keys from the rest of the larger network. In that location are 3 main items to consider: One time Concrete Security and Logical Security are addressed, the final component is user roles and privileges. The core concept promulgated by NIST is the concept of least privilege: where you restrict "the access privileges of authorized personnel (due east.m., program execution privileges, file modification privileges) to the minimum necessary to perform their jobs." NIST gives guidance, in Sections 5.3.v of Recommendation for Cardinal Management – Part 2, on the admission controls and privileges necessary to properly manage user access to the key management system. Beyond limiting access to the key management server, yous should also limit access to the keys themselves based on user and group. The users and grouping access tin be defined on a system level, or at the level of each fundamental. When you create a fundamental yous tin can ascertain the restrictions on user and group admission. As an instance: There is an AES encryption key available on the key direction server used to protect an employee'due south personal data. It is restricted and then that only members of the Homo Resources grouping can apply that key. So any individual with "Human Resource" defined as their individual or group role tin successfully request that key, all others are turned away. One time y'all have physical security, logical security, and user roles in place, you must also consider business concern continuity. If an intruder does incorporate your information or your production server(due south) are taken offline for a diverseness of reasons, you must be able to bounce back in a relatively brusk time with pre-prescribed steps. Here are a couple definitions to showtime u.s. off: Business Continuity: As divers by ISO 22301:2012 (Section 3.iii), it is the "capability of the organization to keep delivery of products or services at acceptable" levels later on a "confusing incident." Hot failover: In a network surroundings, a hot failover is switching to a fill-in server that is regularly updated from the product server and is set, at whatsoever time, should the production server no longer be able to function normally for any length of time. In the example of cardinal management, each production central direction server should exist mirrored with a high availability server in a geographically separate location in case the production server is compromised and taken offline for whatsoever length of time. As an abbreviated list, here are some features to look for in fundamental direction solutions or what you will want to accost if yous build your own: ^Dorsum to Top The hardware security module (HSM) has been discussed already in "Concrete Security" mostly referred to as the "cryptographic module." Merely, to summarize, a HSM is typically a server with different levels of security protection or "hardening" that prevents tampering or loss. These can be summarized as: With many organizations moving some or all of their operations to the cloud, the need for moving their security has also arisen. The good news, many key management providers accept partnered with cloud hosting providers to rack up traditional HSMs in cloud environments. The same levels of "hardening" would even so utilize, as information technology is a traditional HSM in an offsite surround. Virtual instances of an encryption key director offer a bang-up deal more than flexibility than their HSM counterparts. In many cases, a virtual primal managing director tin be downloaded from a vendor in a matter of minutes and deployed in a virtual environment. An HSM, on the other hand, can take days or weeks being shipped to the site and so requires a concrete installation. Further, virtual instances tin can be installed anywhere that supports the virtual platform that the key manager runs in, VMware, as an example. The downside, of form, is that by it's nature of being virtual with no ready physical components, a virtual cardinal manager's software can only be FIPS 140-2 compliant, merely not validated. Then, if your business need(s) or compliance regulation(s) require FIPS 140-two validation, then a HSM is your only option. That being said, the logical security that FIPS 140-ii compliant virtual key managers provide is normally more than than enough for most organizational needs. Cloud providers, such as Amazon Web Services (AWS), Microsoft Azure (Azure), and more than have market offerings for encryption key management every bit well as their own cardinal direction every bit a service (KMaaS). AWS and Azure'due south KMaaS is typically multi-tenant, meaning more i user'southward key(s) are nowadays on the same key management example. This can raise concerns for organizations that need dedicated services to mitigate security concerns of other users accessing the same key data stores. To combat this upshot, well-nigh deject providers will also offer dedicated services. In their marketplaces, there are also contained vendors that provide dedicated services that typically come up in ii forms: Pay-Per-Usage and "bring your ain license." Townsend Security provides for both platforms and for both licensing models: Alliance Key Manager for AWS and Alliance Primal Manager for Azure. Both the AWS and the Azure instances are dedicated key managers in an IaaS virtual case and also enjoy the flexibility of existence the same key managing director that is deployed equally an HSM, Cloud HSM, and VMware case so that your environment can calibration by AWS and Azure, if needed. This is useful for organizations with existing (or futurity) physical information center(s), because having the same technology secure your data everywhere reduces complexity for your It staff equally they use and maintain it. ^Back to Top A very unproblematic internal PKI installation (equally shown in the graphic would menstruation similar this: Equally defined past NIST in, "Introduction to Public Key Technology and the Federal PKI Infrastructure", the PKI surround consists of: Below is a curated list of what OASIS further defines in Department 4 as what the key management client can request of the key management server: For further reading on KMIP, try the KMIP Usage Guide Version 1.2, Edited by Indra Fitzgerald and Judith Furlong. ^Back to Top In Section 3.v of PCI DSS, organizations that process, shop, or transmit cardholder data should, "document and implement procedures to protect keys used to secure stored cardholder information against disclosure and misuse." This includes: Also, Department 3.6 requires that you "fully document and implement all key management processes and procedures for cryptographic keys used for encryption of cardholder information." This includes securely: As a function of this mission the system has published a document, "Security Guidance For Critical Areas of Focus In Cloud Computing," to help vendors and customers achieve more secure applications in cloud environments. The published guidance is now in its 3rd edition and is available from the organization'southward web site. The guidance provides recommendations for encryption key direction in the section "Domain eleven – Encryption and Primal Management". Here are the three chief points that the CSA stresses for encryption key management: Here also is a curated list of their requirements for encryption and fundamental direction: Article 32 also calls for "the pseudonymisation and encryption of personal data." If an system does then, Commodity 34 states that the strict data breach disclosure laws of Article 33 will not be enforced if, The GDPR places a high priority on protecting data at rest with encryption. Since encryption central management is part of an overall encryption strategy, it should be considered part in parcel with complying with EU police force. ^Dorsum to Height Encryption has been effectually for millenniums. Some of the earliest mentions of it come up from the Arthashastra, a treatise on Imperial Indian governance written c2nd century BCE. In it, information technology describes giving messages to state spies in "secret writing". Later, and in arguably the nearly famous class of aboriginal encryption, Julius Caesar sent messages to his battle front end generals in lawmaking. Known as the Caesar Cipher, information technology is a: Unfortunately for Caesar, and fortunately for his opponents, once the zippo is known, all messages can be easily read. Thus rendering the cipher useless. There needed to be a better manner. Fast forward to the electronic historic period. In the 1921 Edward Hebern patented the Hebern Electrical Super Code Naught Machine. It was the first to code the bulletin with a cloak-and-dagger key embedded in a detachable rotor. In recently declassified documents, the NSA showed that the machine enciphered the message by having the operator type the message in and the ciphertext would announced in a calorie-free-board, one alphabetic character at a time. But since the encryption fundamental was limited by the use of one rotor, consisting of 26 circuit points, it was ultimately broken by cryptanalysis, specifically letter frequencies. The real leap frontward was the Enigma Automobile of World War Ii, adult past the Germans in the 1920s. It used three rotors and was thought unbreakable since the Germans, during the war, changed the rotors once a mean solar day, "giving 159 million million million possible settings to choose from," estimates Bletchley Park. But, the Enigma machine was compromised past the Poles in 1932 using mathematical techniques. After, this early work was used to read encrypted messages during World War Two by, among others, Alan Turing (at Bletchley Park) and the use of the then latest data crunching computers. Sending letters deeply had come a long way from simple substitution ciphers. Keys were at present being used - merely they could be croaky using the brute strength of the latest computers. Enter: Information Encryption Standard. Kickoff published as the FIPS 46 standard in 1977, in 1987 the Us Government, under the Calculator Security Human action, mandated that the National Constitute of Standards and Technology (NIST) issue the Information Encryption Standard (DES) in which it "specifies two FIPS approved cryptographic algorithms." It likewise mandated that the "DES key consists of 64 binary digits ("0"s or "i"s) of which 56 bits are randomly generated and used straight by the algorithm. The other viii $.25, which are non used by the algorithm, may exist used for mistake detection." DES was considered very secure at the time. But in little more a decade, and equally computers became exponentially faster, DES keys quickly became vulnerable to creature force attacks. Ii options were proposed to address the result effectually the same time. The offset, introduced in 1997, was Triple Data Encryption Algorithm (TDEA) or as it is more commonly know: Triple Information Encryption Standard (3DES). Equally NIST describes the cryptographic technique: But 3DES, when using but 112 bits, is nonetheless vulnerable to attacks such every bit chosen-plaintext attacks. Too, since 3DES is a multi-step encryption procedure using ii or iii encryption keys, a stronger, more efficient method was needed. In 1997 NIST started a procedure to place a replacement for DES. NIST invited cryptography and information security specialists from around the globe to participate in the discussion and choice process. V encryption algorithms were adopted for study. Through a process of consensus the encryption algorithm proposed past the Belgian cryptographers Joan Daeman and Vincent Rijmen was selected. Prior to pick Daeman and Rijmen used the name Rijndael (derived from their names) for the algorithm. After adoption the encryption algorithm was given the name Advanced Encryption Standard (AES) which is in common use today. In 2000 NIST formally adopted the AES encryption algorithm and published it equally a federal standard under the designation FIPS-197. AES encryption uses a single key equally a role of the encryption process. The central tin can exist 128 bits (xvi bytes), 192 $.25 (24 bytes), or 256 bits (32 bytes) in length. Given that the fastest figurer would have billions of years to run through every permutation of a 256-flake key, AES is considered an extremely secure encryption standard. This brings us to today. AES is a very sophisticated encryption standard with an encryption fundamental and tin withstand the onslaught of the fastest computers. It's only vulnerability? The encryption keys falling into the incorrect hands. That is why, after you take deployed your encryption, your best line of defence is a robust encryption key management strategy. ![]()
![]()
![]()
![]()
What is Encryption Fundamental Management?
Shortcuts
Introduction
"The proper management of cryptographic keys is essential to the constructive use of cryptography for security. Keys are analogous to the combination of a prophylactic. If a rubber combination is known to an adversary, the strongest safe provides no security against penetration. Similarly, poor key management may easily compromise strong algorithms."
~ NIST Recommendation for Primal Management
NIST's argument paints an accurate picture. Like a safe's combination, your encryption keys are only every bit good as the security you use to protect them. There is an unabridged concrete and digital cryptosystem that must exist must be accounted for every bit well as each central's total lifecycle. Therefore, a robust encryption key management system and policies includes:
Types of Encryption Keys
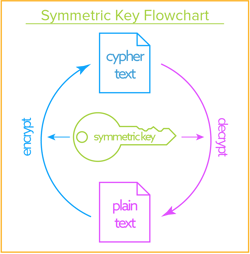
Symmetric Keys: Data-at-Rest
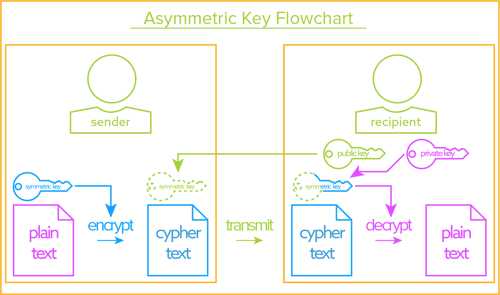
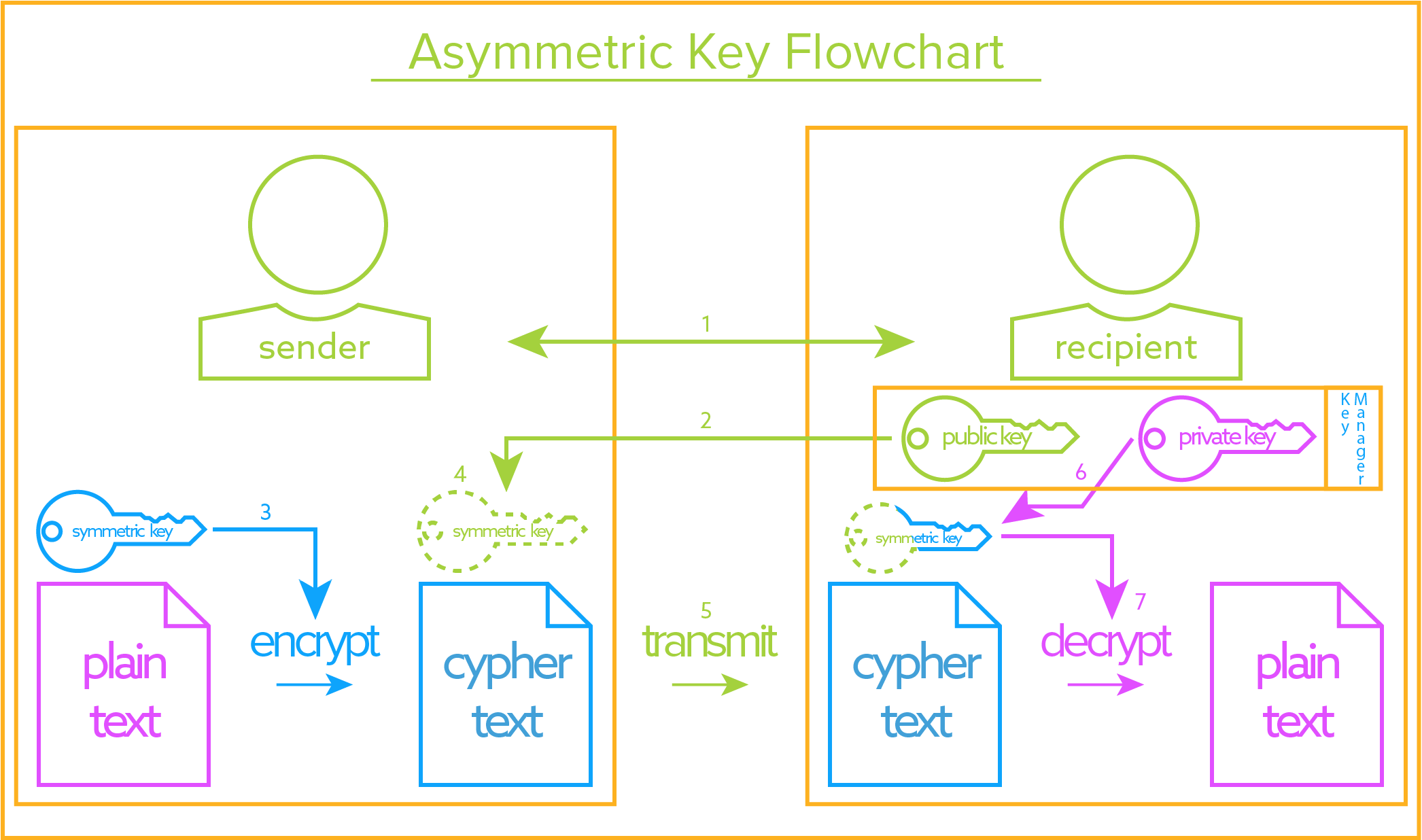
Asymmetric Keys: Information-in-Motion
How Encryption Central Systems Work
Symmetric Key Systems
![]() This is an interactive graphic, click on the numbers higher up to learn more about each step
This is an interactive graphic, click on the numbers higher up to learn more about each step
Disproportionate Central Systems
The Full Life-Cycle of Keys
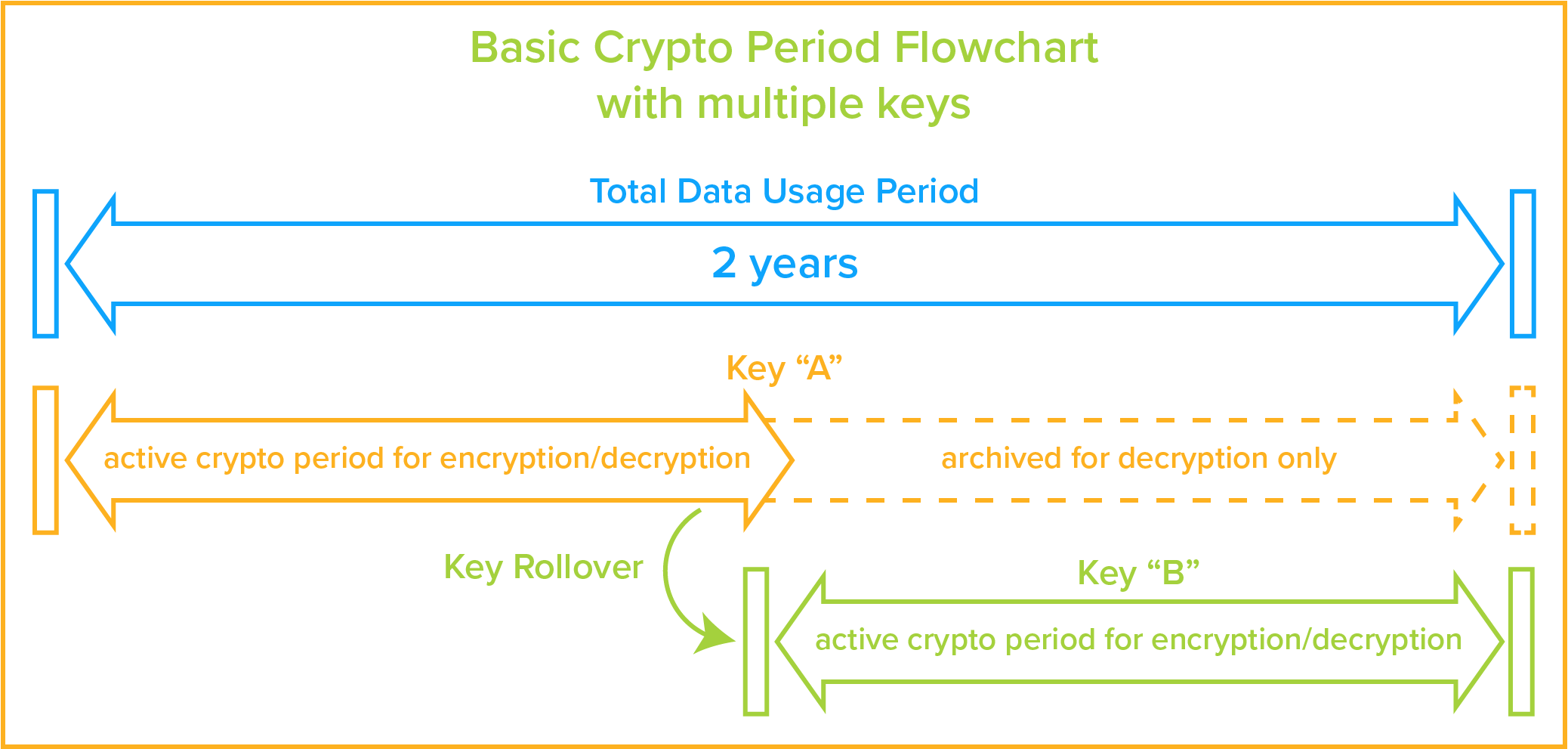
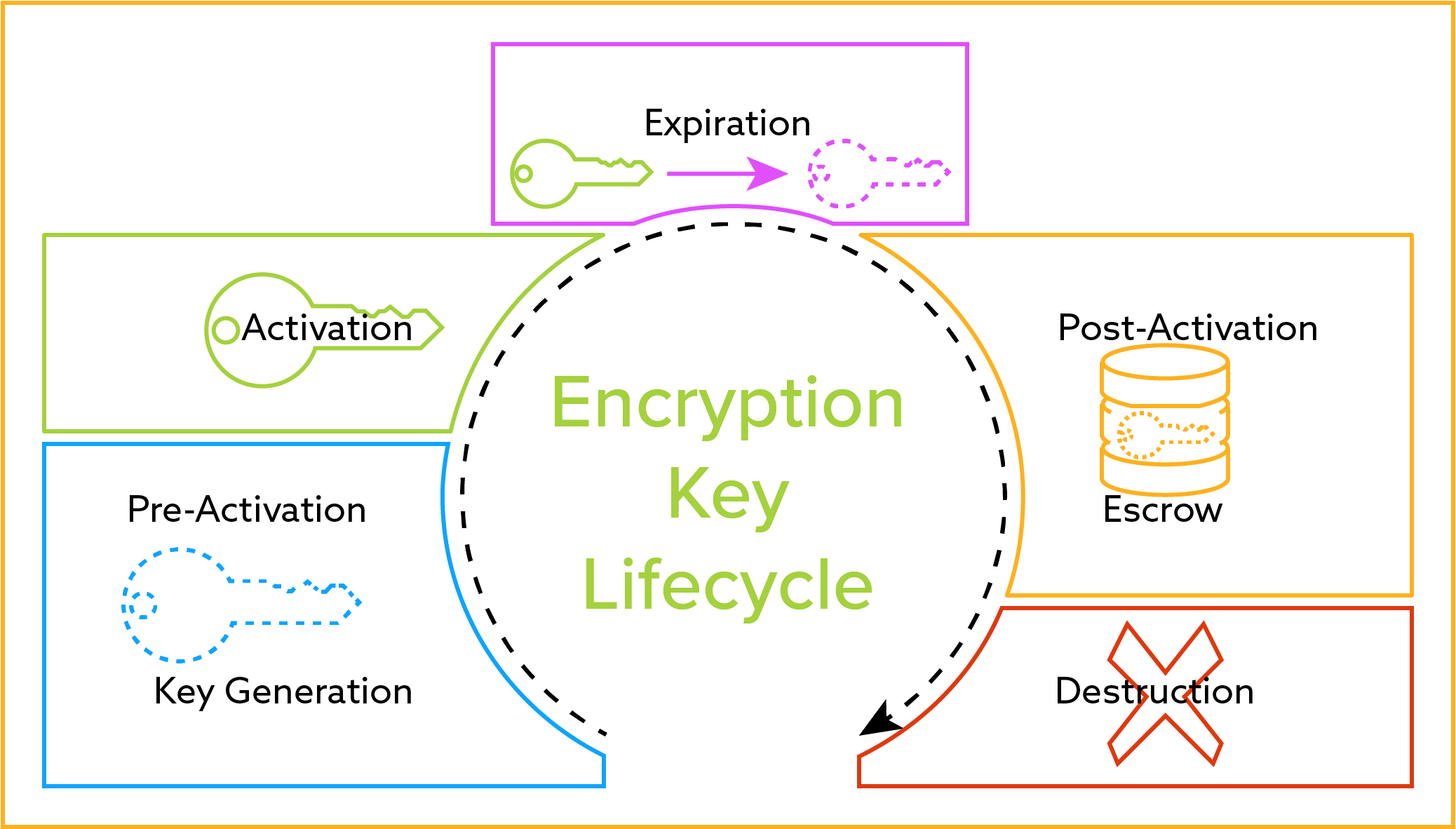
Key Creation (Generation & Pre-Activation)
Key Utilize and Rollover (Activation through Postal service-Activation)

The key manager should let an activated cardinal to be retrieved past authorized systems and users for encryption or decryption processes. It should also seamlessly manage current and past instances of the encryption key. For case, if a new key is generated and the old one deactivated (or rolled) every year, then the fundamental manager should retain previous versions of the fundamental just dispense only the electric current instance and activate previous versions for decryption processes. Previous versions can even so be retrieved in gild to decrypt data encrypted with such versions of the key. The key managing director will too roll the primal either through a previously established schedule or permit an administrator to manually curlicue the central.Cardinal Revocation
Support (Escrow)
Key Deletion (Destruction)
Segregated Roles in Primal Management
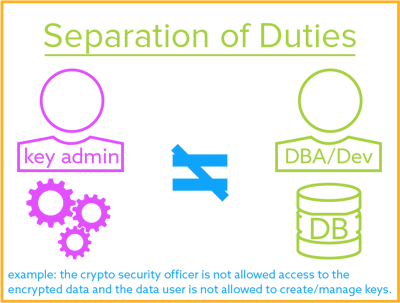
Separation of Duties
A security principle that divides critical functions amid different staff members in an attempt to ensure that no one individual has enough information or access privilege to perpetrate dissentious fraud.
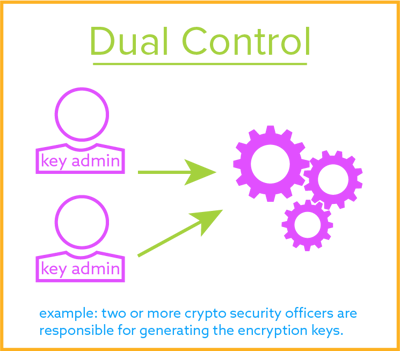
Dual Control
A process that uses two or more than separate entities (usually persons) operating in concert to protect sensitive functions or information. No unmarried entity is able to admission or use the materials, e.one thousand., cryptographic keys.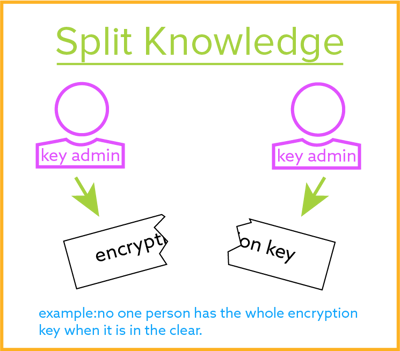
Split up Cognition
The Domains to Secure Encryption Keys
Physical Security
"Concrete and environmental security controls" should exist "implemented to protect the facility housing system resources, the system resource themselves, and the facilities used to support their operation."
How an Encryption Fundamental Manager is Validated
 Logical Access Security
Logical Access Security
User/Office Access
High Availability and Business Continuity
Platforms for Housing the Primal Manager
HSM
Hosted HSM
Virtual
 AWS, Microsoft Azure, and More: Dedicated or "as a Service"
AWS, Microsoft Azure, and More: Dedicated or "as a Service"Communication Protocols
PKI
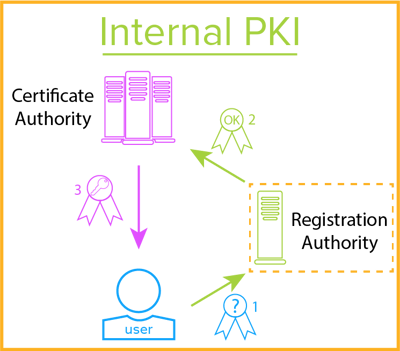 Public key infrastructure (PKI): NIST defines PKI as an infrastructure that "binds public keys to entities, enables other entities to verify public cardinal bindings, and provides the services needed for ongoing management of keys in a distributed system." Put another mode, it is a cryptographic infrastructure consisting of the software, hardware, roles, procedures, and policies needed to properly manage and distribute public keys (such as a digital certificate) and individual keys.
Public key infrastructure (PKI): NIST defines PKI as an infrastructure that "binds public keys to entities, enables other entities to verify public cardinal bindings, and provides the services needed for ongoing management of keys in a distributed system." Put another mode, it is a cryptographic infrastructure consisting of the software, hardware, roles, procedures, and policies needed to properly manage and distribute public keys (such as a digital certificate) and individual keys.
KMIP
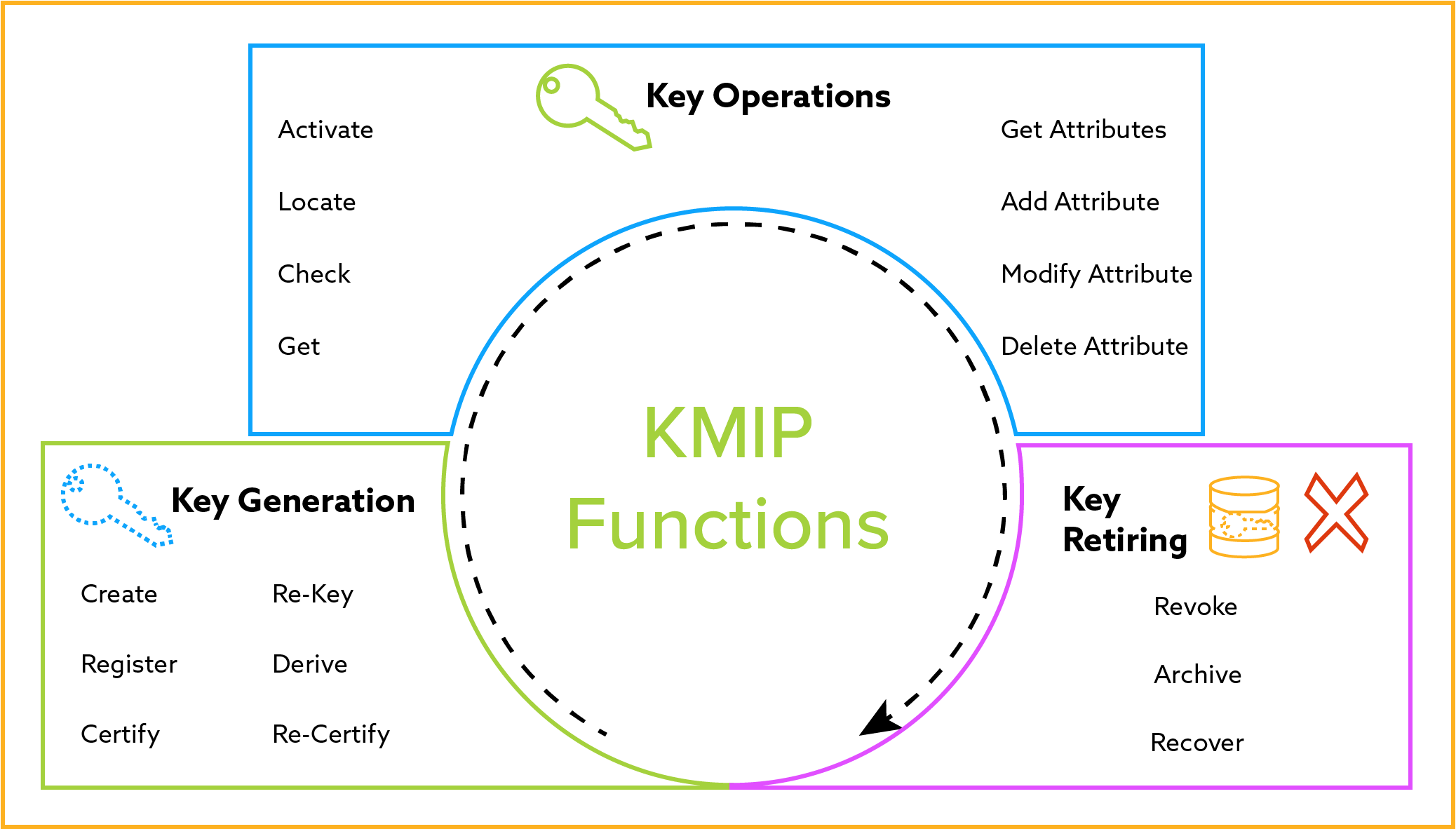 Key Direction Interoperability Protocol (KMIP): As defined past OASIS, KMIP is a communication "protocol used for the communication between clients and servers to perform certain management operations on objects stored and maintained past a key management system." This protocol is a standardized way of managing encryption keys throughout the lifecycle of the key and is designed to facilitate "symmetric and asymmetric cryptographic keys, digital certificates, and templates used to simplify the creation of objects and control their utilise."
Key Direction Interoperability Protocol (KMIP): As defined past OASIS, KMIP is a communication "protocol used for the communication between clients and servers to perform certain management operations on objects stored and maintained past a key management system." This protocol is a standardized way of managing encryption keys throughout the lifecycle of the key and is designed to facilitate "symmetric and asymmetric cryptographic keys, digital certificates, and templates used to simplify the creation of objects and control their utilise."
Encryption Key Management in Meeting Compliance
PCI DSS

 Payment card industry Data Security Standard (PCI DSS) is a widely accepted set of regulations intended to secure credit, debit and cash card transactions and cardholder information. PCI DSS requires that merchants protect sensitive cardholder information from loss and utilize good security practices to discover and protect confronting security breaches.
Payment card industry Data Security Standard (PCI DSS) is a widely accepted set of regulations intended to secure credit, debit and cash card transactions and cardholder information. PCI DSS requires that merchants protect sensitive cardholder information from loss and utilize good security practices to discover and protect confronting security breaches.
HIPAA HITECH
 The Health Insurance Portability and Accountability Act (HIPAA) and the Health Information Engineering for Economic and Clinical Health (HITECH) Human action both seek greater adoption and meaningful use of health it. Both also lay out guidelines and regulations for proper data security around Electronic Protected Wellness Information (ePHI). Compliance with the HIPAA Security Rules and HIPAA Privacy Rules for ePHI requires the use of security technologies and best practices to demonstrate strong efforts towards complying with this federal regulation.
The Health Insurance Portability and Accountability Act (HIPAA) and the Health Information Engineering for Economic and Clinical Health (HITECH) Human action both seek greater adoption and meaningful use of health it. Both also lay out guidelines and regulations for proper data security around Electronic Protected Wellness Information (ePHI). Compliance with the HIPAA Security Rules and HIPAA Privacy Rules for ePHI requires the use of security technologies and best practices to demonstrate strong efforts towards complying with this federal regulation.SOX
 The Sarbanes-Oxley (SOX) Act was passed to protect investors from the possibility of fraudulent accounting activities by corporations. The Sarbanes-Oxley Act (SOX) mandated strict reforms to improve fiscal disclosures from corporations and prevent accounting fraud. Sections 302, 304, and 404 of the Sarbanes-Oxley Act mandate that organizations build, maintain, and annually study on the data security and internal controls used safeguard their sensitive data from misuse and fraud.
The Sarbanes-Oxley (SOX) Act was passed to protect investors from the possibility of fraudulent accounting activities by corporations. The Sarbanes-Oxley Act (SOX) mandated strict reforms to improve fiscal disclosures from corporations and prevent accounting fraud. Sections 302, 304, and 404 of the Sarbanes-Oxley Act mandate that organizations build, maintain, and annually study on the data security and internal controls used safeguard their sensitive data from misuse and fraud.Cloud Security Brotherhood
 While the Cloud Security Alliance is not a governmental agency able to levy fines for non-compliance of their standards, it is an not-for-turn a profit organization of cloud vendors, users, and security experts whose mission is "To promote the employ of best practices for providing security assurance within Cloud Computing, and provide pedagogy on the uses of Cloud Computing to help secure all other forms of computing." They currently have over 80,000 members and growing. So conforming to their standards is in the all-time involvement of many companies worldwide.
While the Cloud Security Alliance is not a governmental agency able to levy fines for non-compliance of their standards, it is an not-for-turn a profit organization of cloud vendors, users, and security experts whose mission is "To promote the employ of best practices for providing security assurance within Cloud Computing, and provide pedagogy on the uses of Cloud Computing to help secure all other forms of computing." They currently have over 80,000 members and growing. So conforming to their standards is in the all-time involvement of many companies worldwide.Domain 11 - Encryption & Key Management
EU GDPR
 The new European Marriage Full general Data Protection Regulation (EU GDPR) has at present passed both the Eu Council and Parliament and replaces the earlier Data Protection Directive (Directive 94/46/EC). In Provision 83 it states:
The new European Marriage Full general Data Protection Regulation (EU GDPR) has at present passed both the Eu Council and Parliament and replaces the earlier Data Protection Directive (Directive 94/46/EC). In Provision 83 it states: In order to maintain security and to prevent processing in infringement of this Regulation, the controller or processor should evaluate the risks inherent in the processing and implement measures to mitigate those risks, such as encryption.
the controller has implemented appropriate technical and organisational protection measures, and those measures were applied to the personal data afflicted by the personal data breach, in particular those that render the personal data unintelligible to whatever person who is not authorised to access it, such equally encryption.
CAP 486
 Hong Kong's CAP 486 Personal Information (Privacy) Ordinance requires that all practical steps will be taken to ensure that personally identifiable data, held by a data user, are protected against unauthorized or accidental access. Such considerations should be the kind of data stored and the impairment that could upshot if any of those things should occur; the physical location where the data is stored; and any security measures incorporated into any equipment in which the data is stored.
Hong Kong's CAP 486 Personal Information (Privacy) Ordinance requires that all practical steps will be taken to ensure that personally identifiable data, held by a data user, are protected against unauthorized or accidental access. Such considerations should be the kind of data stored and the impairment that could upshot if any of those things should occur; the physical location where the data is stored; and any security measures incorporated into any equipment in which the data is stored.APPI
 Nippon's Act on the Protection of Personal Data contains policies that are guidelines, but non laws, governing the protection of personal data. Information technology requires that businesses handling personal information should take all necessary and proper measures for the prevention of leakage, loss, or harm.
Nippon's Act on the Protection of Personal Data contains policies that are guidelines, but non laws, governing the protection of personal data. Information technology requires that businesses handling personal information should take all necessary and proper measures for the prevention of leakage, loss, or harm.PA 1988 & PA 2000
 Australia'southward Privacy Human action of 1988 and the Privacy Amendment Act of 2000 govern data security for the Down Under. In information technology, businesses must have all reasonable steps to protect personally identifiable information in its databases from abuse or theft. An organization must also destroy or permanently de‑identify personal information if it is no longer needed.
Australia'southward Privacy Human action of 1988 and the Privacy Amendment Act of 2000 govern data security for the Down Under. In information technology, businesses must have all reasonable steps to protect personally identifiable information in its databases from abuse or theft. An organization must also destroy or permanently de‑identify personal information if it is no longer needed. Bonus Content
A Brief History - the Need for Encryption Central Management

"substitution cipher in which each letter of the alphabet in the plaintext is 'shifted' a certain number of places down the alphabet. For example, with a shift of one, A would exist replaced by B, B would become C, and so on."
[3DES] encrypts each cake three times with the DES algorithm, using either 2 or three unlike 56-bit keys. This approach yields effective key lengths of 112 or 168 bits

![]()
![]()
![]()
![]()
Source: https://info.townsendsecurity.com/definitive-guide-to-encryption-key-management-fundamentals
0 Response to "what security measure can be used to generate and store cryptographic keys"
Postar um comentário